
Customization is also sometimes called “tailoring”.
1. Run the SCAP Workbench
When installed, the SCAP Workbench can be run from the Activities Overview.

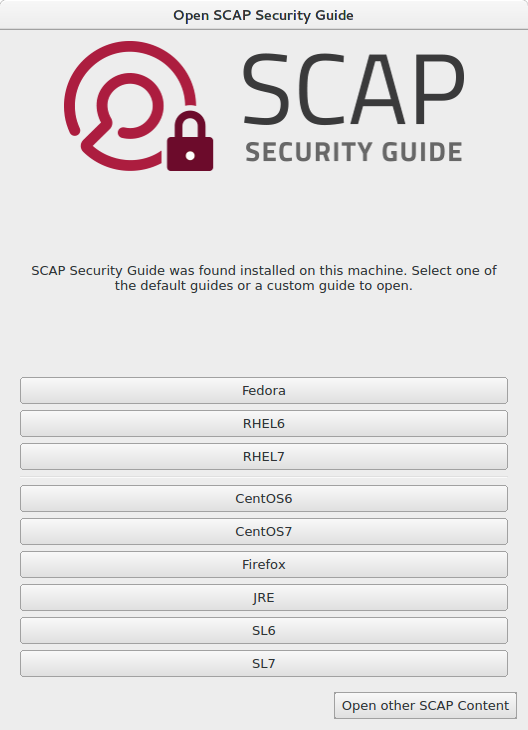
2. Choose a variant for target system
The SCAP Security Guide was automatically installed when you installed the SCAP Workbench. The tool can recognize this and will offer you target platforms of policy. On the following screenshot, click on RHEL6 to choose security guide for Red Hat Enterprise Linux 6.
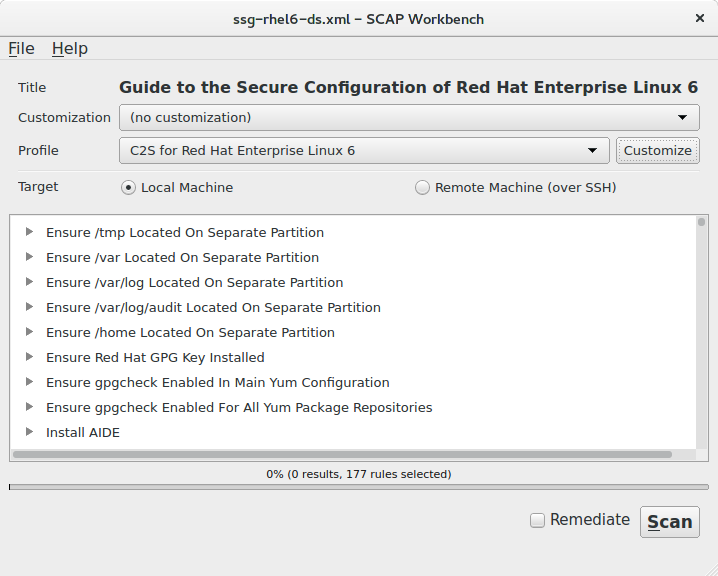
3. Select a profile with desired policy
Main window of the SCAP Workbench has opened and has loaded Guide to the Secure Configuration of Red Hat Enterprise Linux 6. We want now to select the STIG profile now. Click on the Profile combobox and then on Upstream STIG for RHEL6 server.. If you want to customize some different policy, select a different profile in this step.
4. Fork a profile

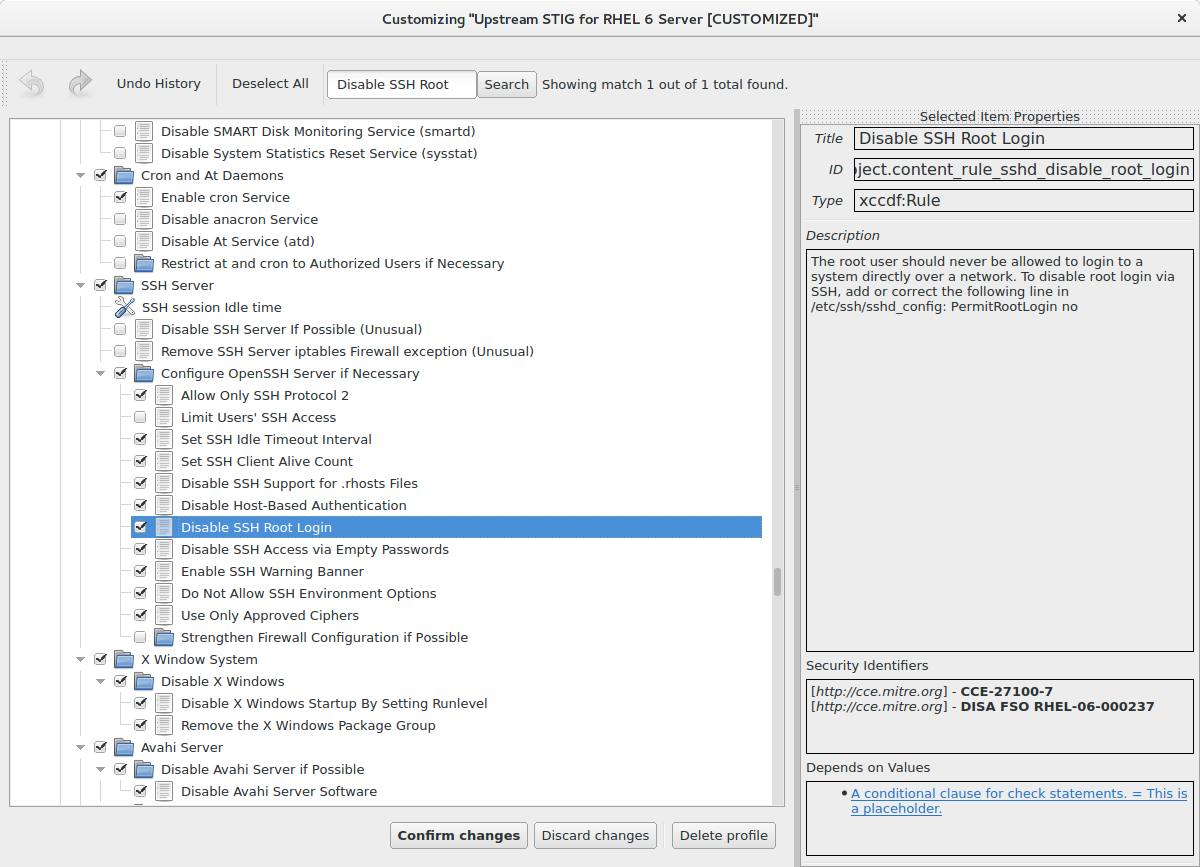
5. Deselect the rule in the Customization dialog
 For faster searching, you can use the Search field above the rule tree. Type “Disable SSH Root Login” to the search field and click on the Search button. Rule will be highlighted.
For faster searching, you can use the Search field above the rule tree. Type “Disable SSH Root Login” to the search field and click on the Search button. Rule will be highlighted.
7. Save your changes to a file
8. Finished!
9. Using the customization file
–tailoring-file TAILORING_FILE
For more information about customization, you can visit our Customization page. For more information about the SCAP Workbench, you can see the SCAP Workbench User Manual
