Stress-free Security for Your IT Infrastructure
The list of security vulnerabilities is constantly growing, and ensuring that your systems are not vulnerable to currently known security flaws is a continuous process.
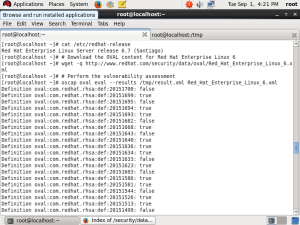
Security researchers are reporting their findings on a daily basis; new weaknesses in software products are constantly being identified either using automated tools designed to uncover security flaws, or while performing code reviews. [1]
Once an exploit [2] [3] [4] for a particular flaw is published, it becomes easy for an attacker to take advantage of the flaw and cause problems such as data leaks or arbitrary code execution. At the same time, known vulnerabilities are also commonly shared in exploit databases.
Any organization wishing to protect itself against these attacks must set up a proper and sustainable vulnerability management policy. A good policy satisfies multiple key concepts, which include:
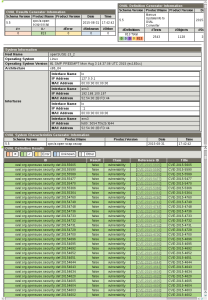
Detailed knowledge of the underlying computer infrastructure
Continuous delivery of certified information about currently known security flaws and their impact
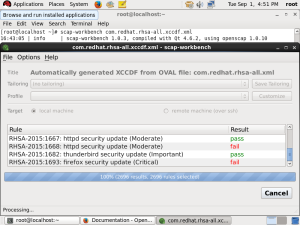
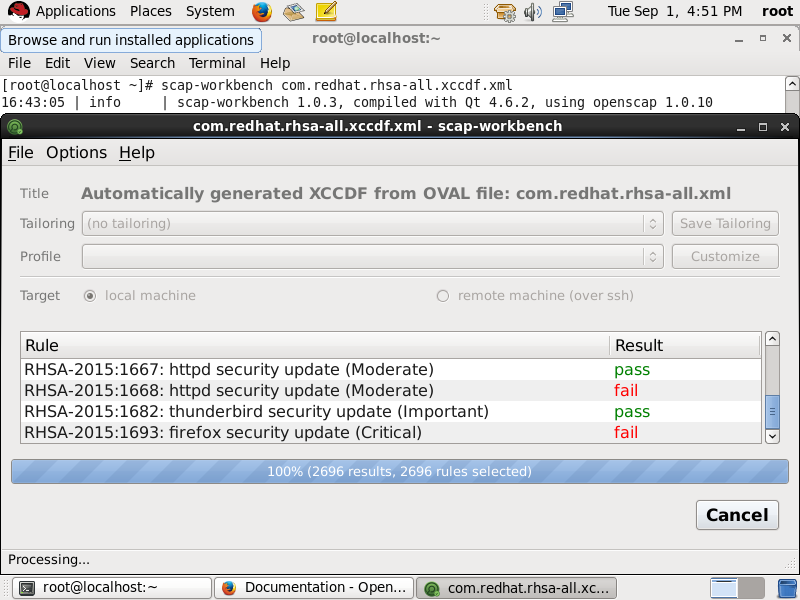
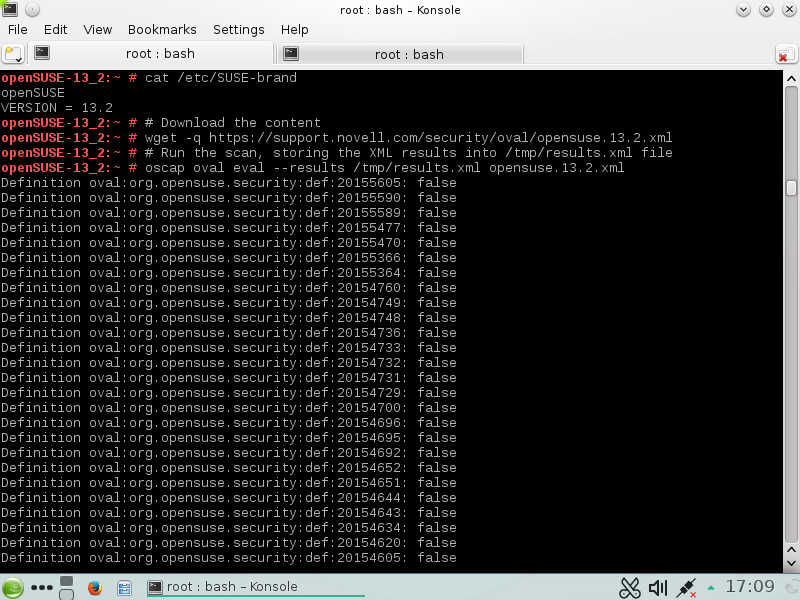
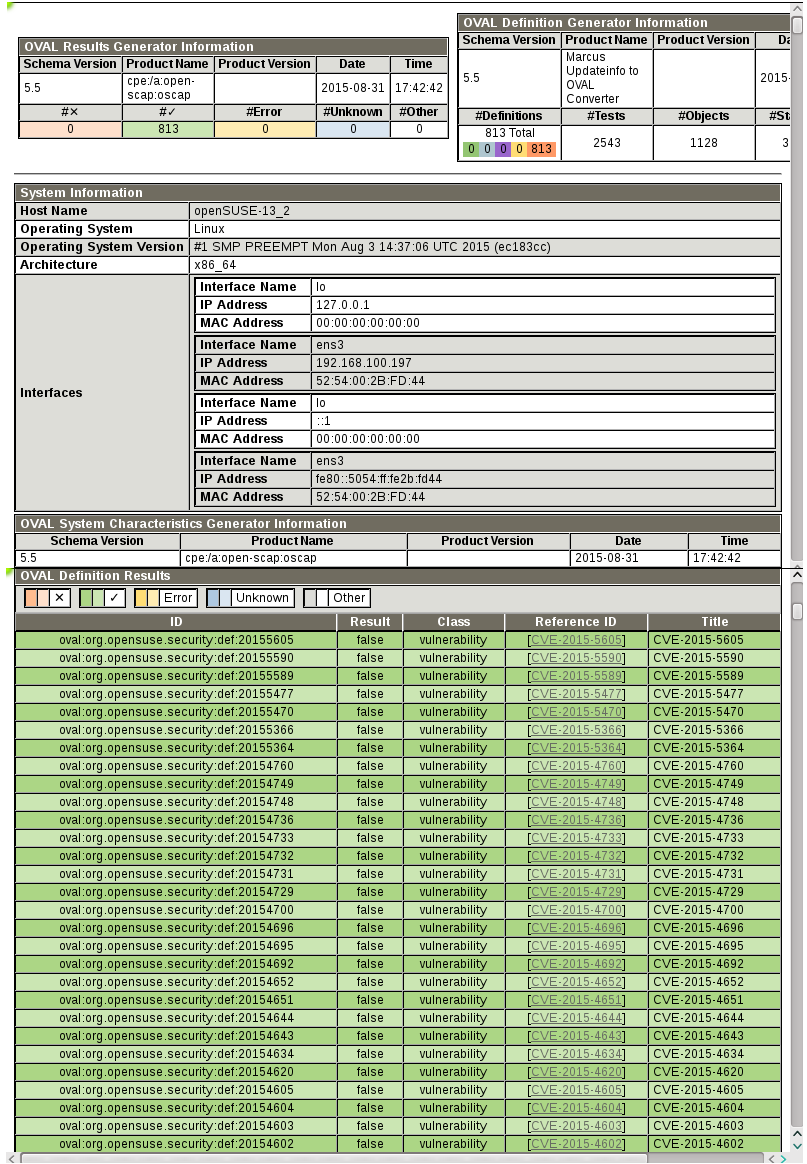
Quick identification of the current security status of each system (security analysis)
Prompt reaction — capability to instantly perform corrective operations where necessary (remedial action)
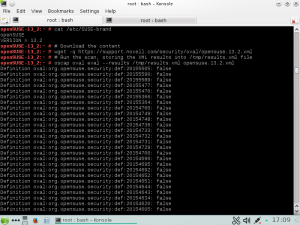
Possibility to perform security analysis in automated,unattended way on regular basis, regardless of the infrastructure’s complexity
Availability of proper software tools to carry out these tasks with minimal effort while preventing or at least minimizing outage periods